10 VoIP Security Best Practices In 2023

As a business owner, it’s your responsibility to ensure the safety and security of your company’s sensitive information.
One way to do this is through the use of Voice over Internet Protocol (VoIP) systems, which allow you to make and receive phone calls over the internet. But like any technology, these systems can be vulnerable to security threats.
That’s why it’s important to implement best practices to protect your company from potential threats. In this article, we’ll dive into 10 VoIP security best practices to keep your business safe in 2023.
From encryption to choosing the right VOIP vendor, these tips will help you safeguard your company’s information and maintain the security of your communication systems.
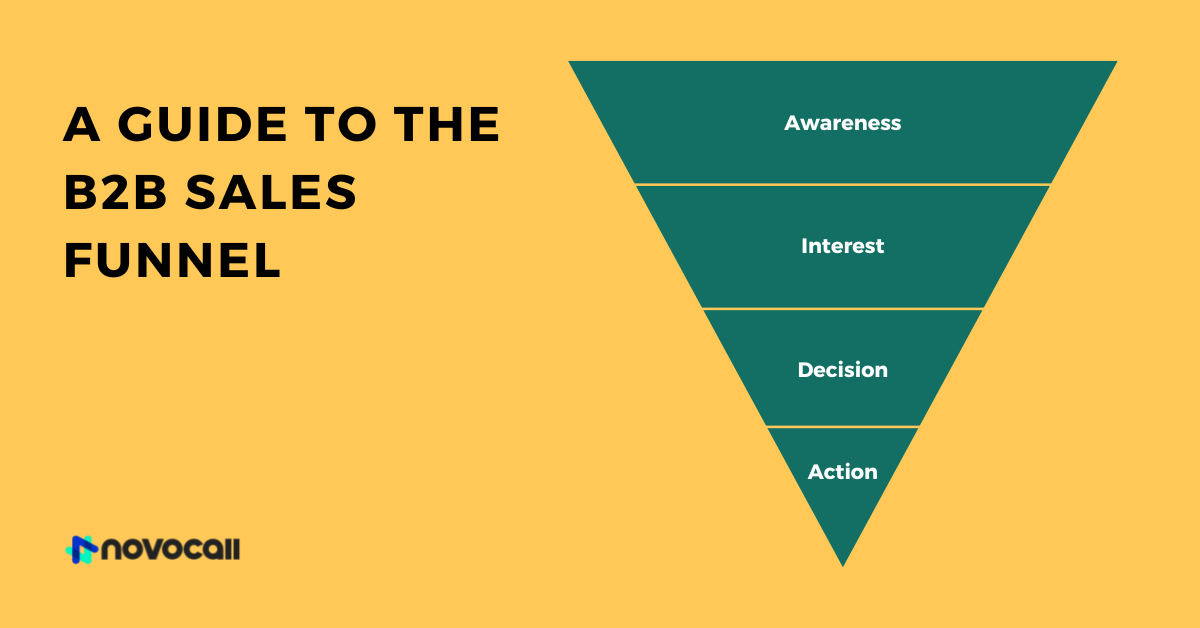
Why care about VoIP security?
According to a recent report, the mobile VoIP industry is anticipated to be worth $183.7 billion by 2027.
To be clear, VoIP stands for voice over internet protocol. So a VoIP phone system is basically a device to transfer the sound of your voice via the internet.
Utilizing the internet to transfer calls makes communication more affordable and easy. In fact, a business’s average savings are between 30% and 50% after switching to a VoIP system.
Having said that, VoIP technology also leaves you more exposed to cyber threats. Insufficient security can have a detrimental impact on your relations with customers and partners.
Plus, it can interrupt crucial operations and damage your company’s reputation. That’s why it is critical to fortify your VoIP system with essential safety protocols.
By understanding VoIP security protocols in detail, you can set up your VoIP the right way and build up a robust protection mechanism to fight against common risks and threats.
VOIP security best practices
Use the VoIP security strategies below to guide the conversation with your vendor. This will help you put proper safety systems or precautions in place.
1. Update your VoIP system regularly
One important VoIP security best practice is to regularly update your system. Just like with any other technology, it’s important to keep your VoIP system up to date with the latest software and security patches.
By doing so, you can protect your system from the latest security threats and vulnerabilities.
Traditional, on-premise, non-digital phone systems did not require these types of software updates. This is an innocent mistake but can lead to substantial harm to your business eventually.
Your VoIP application should be updated on a regular basis. You can achieve this by delegating the duty of routine system evaluation to your IT support.
Alternatively, you can bring up VoIP software updates in your business review meetings once every three months.
2. Secure remote locations
If your business is spread over multiple locations, maintaining VoIP security across all those locations is crucial. The following measures can help secure specific areas.
Geographical restrictions: Just like establishing your call routes profile with your vendor, it is important to set geographical restrictions.
These limits assist in managing consumption from specific areas and restrict any other entry. If there are connection requests outside the decided geographical restriction, your vendor can put them on a separate list to be verified by you.
Virtual Private Network (VPN) connection: VPN connectivity offers tight VoIP security by assisting in handling different branches of a company, safely linking virtual employees and encrypting your data.
3. Secure passwords
As per a study conducted by Verizon in 2019, 80% of cyber attacks connected to data thefts include leaked usernames and passwords.
Needless to say, having robust password policies is an essential part of VoIP security. Here are a few things you can do in order to prevent compromised login credentials:
Safeguard passwords: Never reveal your username and password to unauthorized people, store sensitive data in unsecured locations, or send via email or some other unprotected mode.
Set up password rules: Implement security procedures so that passwords have a compulsory length of 12 characters. Plus, they should include a mix of capital and small letters, numerals, and symbols.
In case of any data breaches, notify your vendor instantly to create new login passwords.
4. Shield yourself from identity fraud
An AARP 2021 report states that 229 million Americans experienced internet fraud in the last 12 months.
Another report from Norton in 2021 found that 6 out of 10 individuals are afraid of having their identity stolen.
To make sure that you don’t fall into the same trap through your VoIP system, you can implement the following measures:
Access lists: These lists allow vendors to restrict access to consumer data in order to guard against identity fraud or scams. The vendor verifies the consumer’s IP address with the one recorded in the vendor’s database to protect against identity theft.
Call routes: Setting up call routes lets your vendor create an account through which only you are allowed to share outbound traffic on your preferred pathways.
Limit call redirecting settings: A prominent function of VoIP communication devices, call forwarding provides a possibility for criminal activity as well.
So think about limiting your call redirecting options on extensions. Ask for help from your vendor to implement your desired configuration settings.
5. Make use of VOIP data encryption
Among the most frequently occurring risks associated with VoIP communications is eavesdropping.
Attackers utilize this approach to snoop in on calls and steal audio data straight from live conversations. As a result, they can acquire confidential details like call source, login credentials, and bank information.
One more thing that you have to worry about is call tampering. This is where hackers interrupt active calls by transmitting huge volumes of data packets down the connection or by slowing the information transfer.
These attacks lead to bad connectivity and extended pauses, which can seriously hinder a business’ capability to run efficiently. To avoid these issues, most well-known VoIP service providers offer encryption capabilities.
Encryption is the process of encoding data so that it can only be accessed by authorized users. By encrypting this data, you can protect it from being intercepted and accessed by unauthorized individuals.
End-to-end encryption at each terminal ensures that your company functions in a proper and dependable manner. To set it up, you can use transport layer security (TLS) to protect incoming and outgoing data between callers.
Another way is to enforce a secure real-time transport protocol (SRTP) to encrypt the data transmitted during conversations. This makes it extremely difficult for attackers to decode the information.
6. Configure account verification
Every device consists of a distinctive IP address. This numerical label recognizes that device when it tries to connect with the network. Using these identifiers, you can block everyone out of the network except your agents.
In case you are working with virtual employees, you can set up IP blacklists. With these lists, you can define criteria to restrict IP addresses with unsuccessful password attempts.
7. Have a crisis management plan
38% of small-sized companies lack predefined rules to tackle cybersecurity risks, says a 2019 report by IFA.
In addition to implementing best practices and taking preventive measures, it’s also important to have a crisis management plan in place for VoIP security.
Set up a crisis strategy. Teach your team the ways to manage the crisis in case your network crashes. Employing the right measures in an emergency may prevent it from getting out of hand.
This strategy should outline the steps to take in the event of a security breach or other emergency situation.
This could include steps such as disconnecting the affected system, alerting relevant parties, and conducting a thorough investigation. By having a plan in place, you can minimize the damage and impact of a security incident and ensure that your company is prepared to handle any potential threats.
It’s important to regularly review and update your crisis management plan to ensure that it remains effective and relevant.
8. Use firewalls to prevent intrusion
A DDoS, also known as distributed denial-of-service, is a malicious attack where hackers deliberately overload a server with information and consume its entire resources.
Such an attack can result in an increased number of dropped calls. It can also block incoming and outgoing calls altogether. The result? A significant impact on a business’s everyday activities, along with its sales.
Now the question is, how can you protect yourself from DDoS attacks?
First of all, prepare in advance by keeping an overprovision bandwidth. Of course, some extra bandwidth will not stop a DDoS attack. But it will buy you extra time to solve the problem.
Another best practice is to implement a clustered firewall. It can ensure longer uptime and capacity, low latency, and reliable connectivity.
The final measure is to use an intrusion prevention system (IPS) to keep track of server usage. A load analysis can detect when the number of sessions exceeds a predefined limit.
The IPS can also terminate connections whenever required to prevent the service quality from dropping.
On top of that, the intrusion detection solutions scan traffic packets to identify and limit system infiltration and secure consumer data.
9. Implement call behavior monitoring
Vishing, similar to phishing but for VoIP, is a scam tactic in which a person uses forged identities and deceives callers into sharing confidential information.
An excellent way to avoid becoming a victim of vishing attacks is to validate every inbound call, even if the call appears to be originating from inside your company’s network.
Next, you can enable the option to record calls coming or going from your VoIP systems. Depending on your VoIP system, you can find this feature in your user interface.
By checking call recordings on a regular basis, you can easily discover abnormal traffic like irregular call locations, call durations, or the profiles conducting this activity.
10. Set credit limits to avoid phreaking
Approximately 46% of illegally made calls across the globe involve VoIP technology, says a 2019 study by VoipReview. This is commonly referred to as VoIP fraud, toll fraud, or phreaking.
It occurs when attackers make their way into your VoIP network and use your services and bandwidth without authorization. Once they are in, they can add extra credits, change your plans, or increase the number of calls. This can lead to additional charges to your VoIP account.
Here’s what you can do to protect your business from phreaking:
Restrict international calling facility to only those who make an explicit request for it. Plus, set time-bound spending limits on international calls.
Introduce credit limits based on historical and current spending. This way, your VoIP vendor could limit any misuse overlooked by other monitoring systems.
Monitor the network for any off-hours usage increases and investigate immediately when there’s an anomaly.
11. Be proactive in handling malware
In a report by JPMorgan, almost 50% of organizations surveyed said that malware is their greatest cybersecurity challenge.
Malware and computer viruses are a serious threat to any network. And VoIP systems are no exception.
The most common way to spread malware is through email. This is because it just takes one simple click by an unsuspecting employee to download it by accident and infect the entire network.
The best way to handle malware attacks is to use a robust defense and monitoring system that keeps an updated repository of known malware.
Additionally, it’s important to educate your employees about the dangers of malware and how to avoid it, such as by avoiding suspicious emails and websites. By being proactive in handling malware, you can help protect your VoIP system and prevent security breaches.
By being proactive in handling malware, you can help protect your VoIP system and prevent security breaches.
Final thoughts on VoIP security
As we discussed, a cloud-based VoIP can deliver numerous operational advantages. But these benefits come with certain security risks. So VoIP security warrants to be one of your top concerns.
Use this list of VoIP security best practices to guide the conversation with your VoIP service provider and put necessary measures in place. And keep monitoring your VoIP security on a regular basis.
Conducting security audits frequently may seem unnecessary, but it’s crucial to prevent any mishaps down the line. And it will help both you and your customers make the most of VoIP technology.

Hitesh Sahni
Hitesh Sahni is a marketing consultant, copywriter, and founder of Smemark.
Related articles